Configure SAML authentication
Security Assertion Markup Language (SAML) authentication allows you to use common external identity providers (IdP) to authenticate usernames and passwords for Webex WFO, the service provider (SP). This method of user authentication and password management is commonly referred to as single sign-on (SSO).
After SAML authentication is configured through your external IdP, the metadata needs to be downloaded, exported, and configured in Webex WFO. See Set up IAM authentication for information on configuring your IdP in Webex WFO.
Login Pages — The login page you use is determined by your organization. See the "Identify your login page" procedure in Log in to Webex WFO with your subdomain URL for more information.
IMPORTANT If you are configuring a new IdP or modifying your existing IdP configuration in any way after October 14th 2025 then you need to locate and use the Assertion Consumer Service URL, Metadata URL, Service Provider Entity ID, and Service Provider Initiated Sign-On URL read-only fields located on the IAM Authentication page.
The IAM Authentication page contains read-only fields for Entity ID, Assertion Consumer Service URL, Metadata URL, and Service Provider Initiated Sign-On URL that are unique to your organization's tenant account. These fields are visible if you select the Enable IAM External Authentication Entity (Company Login) check box under Service Provider. It's important that you know the location of these fields if you are configuring an external IdP.
Webex WFO integrates with IdPs that support SAML 2.0 authentication (see Set up IAM authentication for the list of supported IdPs). The following general parameters apply when configuring the SAML assertion in an IdP.
| Assertion Component | Configuration |
|---|---|
|
Attributes |
The IdP must send an assertion containing your users’ email address as an attribute. This email address must match the email address used for Webex WFO authentication. Attribute names are case sensitive. EXAMPLE
The specific name of the email attribute depends on the IdP that you use. The following are examples:
|
|
Signatures |
The SAML assertion must be signed. The signing key is provided in the XML data. The SAML assertion signature algorithms are listed below.
|
|
Key sizes |
Encrypted assertions are supported only with a maximum key size of 128 bits. |
Prerequisites
You need to set up an application for Cisco IAM (identity and access management) in your IdP. The following list contains values required to setup this application.
-
Assertion Consumer Service URL. After you successfully authenticate with your IdP, the user is redirected to this URL with the SAML response. The URL varies depending on your organization. Use the domain for your region in the list below or the Assertion Consumer Service URL value located on the IAM Authentication page if your organization uses a subdomain-based URL after October 14th 2025.
IAM Domain Names Australia
https://id-aus.calabriocloud.com/am/Consumer/metaAlias/bravo/calabriospCanada
https://id-ca.calabriocloud.com/am/Consumer/metaAlias/bravo/calabriospEuropean Union
https://id-eu.calabriocloud.com/am/Consumer/metaAlias/bravo/calabriospUnited Kingdom
https://id-uk.calabriocloud.com/am/Consumer/metaAlias/bravo/calabriospUnited States https://id.calabriocloud.com/am/Consumer/metaAlias/bravo/calabriospSingapore
https://id-sgp.calabriocloud.com/am/Consumer/metaAlias/bravo/calabriosp - Service Provider Entity ID:
- Your Service Provider Entity ID is a unique value if you are configuring your IdP after September 30th 2025. To locate and copy your Service Provider Entity ID, navigate to Application Management > IAM Authentication > Service Provider Settings > Entity ID.
- Your Service Provider Entity ID is calabriosp if your IdP was configured prior to October 14th 2025.
- The email address must be passed in an attribute named "mail".
-
If the SAML request needs to be signed, the signing certificate for it can be found in the Cisco Identity and Access Management (IAM) Service Provider metadata for your region that’s detailed below or in the read-only Metadata URL field on the IAM Authentication page in Application Management if you use a subdomain-based log in URL after October 14th 2025.
IAM Service Provider Metadata Australia
https://id-aus.calabriocloud.com/am/saml2/jsp/exportmetadata.jsp?entityId=calabriosp&realm=bravoCanada
https://id-ca.calabriocloud.com/am/saml2/jsp/exportmetadata.jsp?entityId=calabriosp&realm=bravoEuropean Union https://id-eu.calabriocloud.com/am/saml2/jsp/exportmetadata.jsp?entityId=calabriosp&realm=bravoUnited Kingdom
https://id-uk.calabriocloud.com/am/saml2/jsp/exportmetadata.jsp?entityId=calabriosp&realm=bravoUnited States https://id.calabriocloud.com/am/saml2/jsp/exportmetadata.jsp?entityId=calabriosp&realm=bravoSingapore
https://id-sgp.calabriocloud.com/am/saml2/jsp/exportmetadata.jsp?entityId=calabriosp&realm=bravo -
(Optional) Service Provider initiated Sign-on URL. When a user opens this URL, the service provider, Cisco, redirects to your IdP to authenticate and sign on the user. This is not required for most IdPs.
Use the Cisco IAM Service for your region, or use the read-only Service Provider Initiated Sign-On URL field on the IAM Authentication page in Application Management if you use a subdomain-based log in URL after October 14th 2025.
IAM Service Australia
https://id-aus.calabriocloud.com/am/saml2/jsp/spSSOInit.jsp?metaAlias=/bravo/calabriosp&idpEntityID=[IDP_ENTITY_ID_URL_ENCODED]Canada
https://id-ca.calabriocloud.com/am/saml2/jsp/spSSOInit.jsp?metaAlias=/bravo/calabriosp&idpEntityID=[IDP_ENTITY_ID_URL_ENCODED]European Union https://id-eu.calabriocloud.com/am/saml2/jsp/spSSOInit.jsp?metaAlias=/bravo/calabriosp&idpEntityID=[IDP_ENTITY_ID_URL_ENCODED]United Kingdom
https://id-uk.calabriocloud.com/am/saml2/jsp/spSSOInit.jsp?metaAlias=/bravo/calabriosp&idpEntityID=[IDP_ENTITY_ID_URL_ENCODED]United States https://id.calabriocloud.com/am/saml2/jsp/spSSOInit.jsp?metaAlias=/bravo/calabriosp&idpEntityID=[IDP_ENTITY_ID_URL_ENCODED]Singapore
https://id-sgp.calabriocloud.com/am/saml2/jsp/spSSOInit.jsp?metaAlias=/bravo/calabriosp&idpEntityID=[IDP_ENTITY_ID_URL_ENCODED]EXAMPLE In this example for the United States IAM service, <
https://www.example.com/123> is the IDP entity ID that becomes <https%3A%2F%2Fwww.example.com%2F123> when the URL is encoded.https://id.calabriocloud.com/am/saml2/jsp/spSSOInit.jsp?metaAlias=/bravo/calabriosp&idpEntityID=https%3A%2F%2Fwww.example.com%2F123 - You need to assign users or groups who need access to Webex WFO to this application.
The following is an overview of how to configure Okta as your IdP:
- Create an Okta app.
- Configure the Okta app.
After you configure Okta, you have to download a metadata file and save the metadata file (see Export SAML Metadata). Afterward, follow the procedure detailed in Set up IAM authentication to connect your IdP to Webex WFO.
- Log in to Okta.
NOTE You must be a Super Administrator in Okta to create and configure an app.
- Navigate to Applications > Applications.
- Click Add Application.
- Click Create New App.
-
In the Create New Application Integration dialog box, configure the fields as follows.
Field Configuration Platform
Select Web.
Sign on method
Select SAML 2.0.
-
In the General Settings tab, configure the fields as follows.
Field Configuration App name
Enter a unique name for Webex WFO.
App logo
(Optional) Upload an image to identify Webex WFO in Okta.
App visibility
(Optional) Limit who can see the image in Okta.
- Click Next.
-
On the Configure SAML tab, configure the fields as follows.
NOTE If Advanced Settings is hidden, click Show Advanced Settings.
Field Configuration General
Single sign on URL
Copy and paste the Assertion Consumer Service URL that was listed as a prerequisite.
Leave the Use this for Recipient URL and Destination URL check box selected (default).
Audience URI (SP Entity ID)
Copy and paste your Service Provider Entity ID that was listed as a prerequisite.
Name ID format
Select EmailAddress.
Application username
Select Email.
Response
Select Signed.
Assertion Signature
Select Signed.
Signature Algorithm
Select either RSA-SHA1 or RSA-SHA256.
Digest Algorithm
Select either RSA-SHA1 or RSA-SHA256.
Assertion Encryption
Select Unencrypted.
Enable Single Logout
Leave the Allow application to initiate Single Logout check box cleared (default).
Authentication context class
Select PasswordProtectedTransport.
Honor Force Authentication
Select Yes.
SAML Issuer ID
Leave blank.
Attribute Statements
Name
Enter mail.
NOTE This allows a user’s email address to be properly mapped for SAML assertion.
Name format
Select Unspecified.
Value
Select user.email.
NOTE You do not need to configure any attributes in the Group Attribute Statements section.
- Click Next.
-
In the Feedback tab, select the Feedback option that is appropriate to your company’s use of Okta.
NOTE Your choice does not affect the ability of Webex WFO to use Okta as an IdP.
- In the Assignments tab, assign the groups and users that will have access to Webex WFO.
- Click Finish.
The following procedure details how to integrate your OneLogin IdP for Webex WFO Identity and Access Management (IAM) Service Provider (SP).
Configure OneLogin
- Log in to OneLogin as an administrator.
- From the menu bar, go to Applications.
- Click Add App.
- In the App Listing search for the Calabrio ONE app.
- Save your changes.
This section details how to integrate your Active Directory Federation Services (AD FS) IdP for Webex WFO Identity and Access Management (IAM) Service Provider (SP).
The following is an overview of how to configure single sign-on for Active Directory Federation Services (AD FS):
- Configure a Global Authentication Policy.
- Configure Relying Party Trust for your identity provider.
- Configure the LDAP email claim rule for the Webex WFO trust.
- Configure the incoming claim transform email address custom rule for the Webex WFO trust.
- Configure the incoming claim add mail attribute custom rule for the Webex WFO trust.
- Extract your Webex WFO service provider certificate.
- Configure the secure hash algorithm and import your Webex WFO service provider certificate.
- Assign users and/or groups to Active Directory for the AD FS.
- Save your AD FS Federation Metadata XML file.
- Follow the procedure detailed in Set up IAM authentication to connect your IdP to Webex WFO.
Configure Global Authentication Policy
- Open the Windows Server AD FS Management Console.
- Select the Authentication Policies folder.
- Under Global Settings in Primary Authentication, click Edit. The Edit Global Authentication Policy window appears.
- Under the Intranet section in the Primary tab, select the Forms Authentication check box and the Windows Authentication check box. If the check boxes are already selected, click Cancel.
Configure Relying Party Trust for your identity provider
Configuring Relying Party Trust for your identity provider is a multistep procedure.
First, begin the Add Relying Party Trust Wizard.
- Open the Windows Server AD FS Management Console.
- Expand the Trust Relationships folder.
- Right-click the Relying Party Trusts folder, and then click Add Relying Party Trust. The Add Relying Party Trust Wizard appears.
- Click Start.
Next, configure Relying Party Trust with the Add Relying Party Trust Wizard.
- Choose Enter data about the relying party manually, and then click Next.
- Enter “Webex WFO” in the Display name field, and then click Next.
- Choose AD FS profile, and then click Next.
- Click Next on the “Configure Certificate” step. You do not need to specify an optional token encryption certificate.
- On the “Configure URL” step, click the Enable support for the SAML 2.0 WebSSO protocol check box.
- Under Relying party SAML 2.0 SSO service URL, enter the Assertion Consumer Service URL (listed as a prerequisite) in the text field, and then click Next.
- On the “Configure Identifiers” step, enter the Entity ID (listed as a prerequisite) in the Relying party trust identifier text field, click Add, and then click Next.
- On the “Configure Multi-factor Authentication Now?” step, click the I do not want to configure multi-factor authentication settings for this relying party trust at this time check box, and then click Next.
- On the “Choose Issuance Authorization Rules” step, click Permit all users to access this relying party check box, and then click Next.
- On the “Ready to Add Trust” step, click Next.
- On the “Finish” step, click the Open the Edit Claim Rules dialog for this relying party trust when the wizard closes check box.
- Click Close. The Edit Claim Rules for Calabrio ONE window appears.
Configure the LDAP email claim rule for the Webex WFO trust
- Click Add Rule... under the Issuance Transform Rules tab in the Edit Claim Rules window.
- Select Send LDAP Attributes as Claims from the Claim rule template drop-down list, and then click Next.
- Enter “LDAP Email Address” in the Claim rule name field.
- Select Active Directory from the Attribute store drop-down list.
- Select E-Mail Addresses from the LDAP Attribute drop-down list.
- Select E-Mail Address from the Outgoing Claim Type drop-down list.
- Click Finish to complete configuration of this claim rule and add the incoming claim transform rule.
Configure the incoming claim transform email address custom rule for the Webex WFO trust
- Click Add Rule... under the Issuance Transform Rules tab in the Edit Claim Rules window.
- Select Send Claims Using a Custom Rule from the Claim rule template drop-down list, and then click Next.
- Enter “Transform Email Address” in the Claim rule name field.
-
Enter the following in the Custom rule field.
NOTE In the following example, calabriosp is the Entity ID; however, the entity ID value you see may be unique to your organization. Refer to the prerequisites section for details on how to identity your entity ID.
Copyc:[Type == "http://schemas.xmlsoap.org/ws/2005/05/identity/claims/emailaddress"]
=> issue(Type = "http://schemas.xmlsoap.org/ws/2005/05/identity/claims/nameidentifier", Issuer = c.Issuer, OriginalIssuer = c.OriginalIssuer, Value = c.Value, ValueType = c.ValueType, Properties["http://schemas.xmlsoap.org/ws/2005/05/identity/claimproperties/format"] = "urn:oasis:names:tc:SAML:1.1:nameid-format:emailAddress", Properties["http://schemas.xmlsoap.org/ws/2005/05/identity/claimproperties/spnamequalifier"] = "calabriosp"); - Click Finish to complete configuration of this claim rule.
Configure the incoming claim add mail attribute custom rule for the Webex WFO trust
- Click Add Rule... under the Issuance Transform Rules tab in the Edit Claim Rules window.
- Select Send Claims Using a Custom Rule from the Claim rule template drop-down list, and then click Next.
- Enter “Add mail Attribute” in the Claim rule name field.
-
Enter the following in Custom rule field.
Copyc:[Type == "http://schemas.xmlsoap.org/ws/2005/05/identity/claims/emailaddress"]
=> issue(Type = "mail", Value = c.Value); - Click Finish to complete configuration of this claim rule.
- Click OK to finish editing claim rules and close the Edit Claim Rules window.
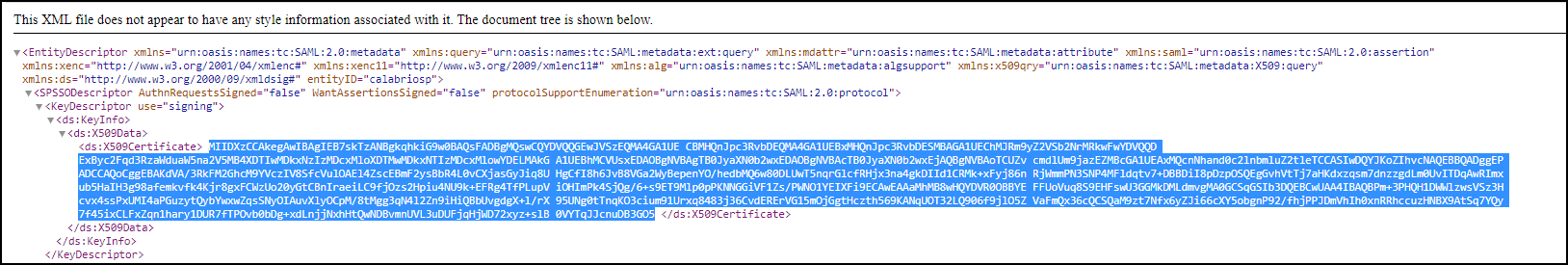
Extract Webex WFO service provider certificate
- In an internet browser, navigate to the IAM Service Provider Metadata URL (listed as a prerequisite).
-
Copy the contents of “X509Certificate” from under SPSSODescriptor > KeyDescriptor use=”signing”> to a file with .cer extension such as EUSigningCert.cer on the AD FS server.
Configure the secure hash algorithm and import Webex WFO service provider certificate
- Open the Windows Server AD FS Management Console.
- Open the Webex WFO trust you created in one of the previous procedures to open the Calabrio ONE Properties window.
- Click the Advanced tab and select SHA-1 from the Secure hash algorithm drop-down list.
-
Click the Signature tab, and then click Add.... Select the Webex WFO service provider certificate created in the previous procedure.
NOTE If the Webex WFO service provider certificate is not listed, you might need to select All files (*.*) in the file-type filter in the lower right corner of the window next to the File name text field.
- Click OK to finish editing the trust properties and close the Calabrio ONE Properties window.
Assign users and groups to Active Directory used for AD FS
Add desired user(s) and group(s) to the Active Directory used for AD FS to grant them access to Webex WFO via AD FS. A user’s email address must match the email address configured for the user in Webex WFO exactly.
Save your AD FS Federation Metadata XML file
Where in the below URL, <ADFS Hostname> is your ADFS hostname.
https://<ADFS Hostname>/FederationMetadata/2007-06/FederationMetadata.xml
AD FS Identity Provider-Initiated Single Sign-On
-
Navigate to the following unique URL in an internet browser.
https://<ADFS Hostname>/adfs/ls/idpinitiatedsignon.aspx
Where in the above URL, <ADFS Hostname> is your ADFS hostname. - Click Sign in to one of the following sites, and select Calabrio ONE from the drop-down list.
- Enter your user credentials in the text fields, and then click Sign in. You are redirected and logged in to the Webex WFO site.
NOTE You can follow the procedure detailed in Set up IAM authentication to connect your IdP to Webex WFO.
Troubleshooting procedures
AD FS event errors
The Event Viewer window displays logs of AD FS authentication issues. You can check past events to investigate errors.
- Navigate to Event Viewer > Applications and Services Logs > AD FS > Admin.
- Click the desired event in the Admin list for more details.
NameId Format in SAMLRequest issue
The NameId Format in SAMLRequest is urn:oasis:names:tc:SAML:1.1:nameid-format:unspecified.
If issues occur, update the Name ID Format field on the IAM Authentication page. See Set up IAM authentication for more information.
NOTE In the following example, calabriosp is the Entity ID; however, the entity ID value you see may be unique to your organization. Refer to the prerequisites section for details on how to identity your entity ID.
Encountered error during federation passive request.
Additional Data
Protocol Name:
Saml
Relying Party:
calabriosp
Exception details:
Microsoft.IdentityServer.Protocols.Saml.InvalidNameIdPolicyException: MSIS7070: The SAML request contained a NameIDPolicy that was not satisfied by the issued token. Requested NameIDPolicy: AllowCreate: True Format: urn:oasis:names:tc:SAML:1.1:nameid-format:emailAddress SPNameQualifier: calabriosp. Actual NameID properties: Format: urn:oasis:names:tc:SAML:1.1:nameid-format:emailAddress, NameQualifier: SPNameQualifier: , SPProvidedId: .
at Microsoft.IdentityServer.Web.Protocols.Saml.SamlProtocolManager.Issue(HttpSamlRequestMessage httpSamlRequestMessage, SecurityTokenElement onBehalfOf, String sessionState, String relayState, String& newSamlSession, String& samlpAuthenticationProvider, Boolean isUrlTranslationNeeded, WrappedHttpListenerContext context, Boolean isKmsiRequested)
at Microsoft.IdentityServer.Web.Protocols.Saml.SamlProtocolHandler.RequestBearerToken(WrappedHttpListenerContext context, HttpSamlRequestMessage httpSamlRequest, SecurityTokenElement onBehalfOf, String relyingPartyIdentifier, Boolean isKmsiRequested, Boolean isApplicationProxyTokenRequired, String& samlpSessionState, String& samlpAuthenticationProvider)
at Microsoft.IdentityServer.Web.Protocols.Saml.SamlProtocolHandler.BuildSignInResponseCoreWithSerializedToken(HttpSamlRequestMessage httpSamlRequest, WrappedHttpListenerContext context, String relyingPartyIdentifier, SecurityTokenElement signOnTokenElement, Boolean isKmsiRequested, Boolean isApplicationProxyTokenRequired)
at Microsoft.IdentityServer.Web.Protocols.Saml.SamlProtocolHandler.BuildSignInResponseCoreWithSecurityToken(SamlSignInContext context, SecurityToken securityToken, SecurityToken deviceSecurityToken)
at Microsoft.IdentityServer.Web.Protocols.Saml.SamlProtocolHandler.Process(ProtocolContext context)
at Microsoft.IdentityServer.Web.PassiveProtocolListener.ProcessProtocolRequest(ProtocolContext protocolContext, PassiveProtocolHandler protocolHandler)
at Microsoft.IdentityServer.Web.PassiveProtocolListener.OnGetContext(WrappedHttpListenerContext context)
Encountered error during federation passive request.
Additional Data
Protocol Name:
Saml
Relying Party:
calabriosp
Exception details:
Microsoft.IdentityServer.Protocols.Saml.InvalidNameIdPolicyException: MSIS7070: The SAML request contained a NameIDPolicy that was not satisfied by the issued token. Requested NameIDPolicy: AllowCreate: True Format: urn:oasis:names:tc:SAML:1.1:nameid-format:unspecified SPNameQualifier: calabriosp. Actual NameID properties: Format: urn:oasis:names:tc:SAML:1.1:nameid-format:emailAddress, NameQualifier: SPNameQualifier: , SPProvidedId: .
at Microsoft.IdentityServer.Web.Protocols.Saml.SamlProtocolManager.Issue(HttpSamlRequestMessage httpSamlRequestMessage, SecurityTokenElement onBehalfOf, String sessionState, String relayState, String& newSamlSession, String& samlpAuthenticationProvider, Boolean isUrlTranslationNeeded, WrappedHttpListenerContext context, Boolean isKmsiRequested)
at Microsoft.IdentityServer.Web.Protocols.Saml.SamlProtocolHandler.RequestBearerToken(WrappedHttpListenerContext context, HttpSamlRequestMessage httpSamlRequest, SecurityTokenElement onBehalfOf, String relyingPartyIdentifier, Boolean isKmsiRequested, Boolean isApplicationProxyTokenRequired, String& samlpSessionState, String& samlpAuthenticationProvider)
at Microsoft.IdentityServer.Web.Protocols.Saml.SamlProtocolHandler.BuildSignInResponseCoreWithSerializedToken(HttpSamlRequestMessage httpSamlRequest, WrappedHttpListenerContext context, String relyingPartyIdentifier, SecurityTokenElement signOnTokenElement, Boolean isKmsiRequested, Boolean isApplicationProxyTokenRequired)
at Microsoft.IdentityServer.Web.Protocols.Saml.SamlProtocolHandler.BuildSignInResponseCoreWithSecurityToken(SamlSignInContext context, SecurityToken securityToken, SecurityToken deviceSecurityToken)
at Microsoft.IdentityServer.Web.Protocols.Saml.SamlProtocolHandler.Process(ProtocolContext context)
at Microsoft.IdentityServer.Web.PassiveProtocolListener.ProcessProtocolRequest(ProtocolContext protocolContext, PassiveProtocolHandler protocolHandler)
at Microsoft.IdentityServer.Web.PassiveProtocolListener.OnGetContext(WrappedHttpListenerContext context)
Missing SPNameQualifier of your Entity ID
If you see the following error message, attempt the Configure the incoming claim transform email address custom rule for the Webex WFO trust procedure again.
NOTE In the following example, calabriosp is the Entity ID; however, the entity ID value you see may be unique to your organization. Refer to the prerequisites section for details on how to identity your entity ID.
Encountered error during federation passive request.
Additional Data
Protocol Name:
Saml
Relying Party:
calabriosp
Exception details:
Microsoft.IdentityServer.Protocols.Saml.InvalidNameIdPolicyException: MSIS7070: The SAML request contained a NameIDPolicy that was not satisfied by the issued token. Requested NameIDPolicy: AllowCreate: True Format: urn:oasis:names:tc:SAML:1.1:nameid-format:emailAddress SPNameQualifier: calabriosp. Actual NameID properties: Format: urn:oasis:names:tc:SAML:1.1:nameid-format:emailAddress, NameQualifier: SPNameQualifier: , SPProvidedId: .
at Microsoft.IdentityServer.Web.Protocols.Saml.SamlProtocolManager.Issue(HttpSamlRequestMessage httpSamlRequestMessage, SecurityTokenElement onBehalfOf, String sessionState, String relayState, String& newSamlSession, String& samlpAuthenticationProvider, Boolean isUrlTranslationNeeded, WrappedHttpListenerContext context, Boolean isKmsiRequested)
at Microsoft.IdentityServer.Web.Protocols.Saml.SamlProtocolHandler.RequestBearerToken(WrappedHttpListenerContext context, HttpSamlRequestMessage httpSamlRequest, SecurityTokenElement onBehalfOf, String relyingPartyIdentifier, Boolean isKmsiRequested, Boolean isApplicationProxyTokenRequired, String& samlpSessionState, String& samlpAuthenticationProvider)
at Microsoft.IdentityServer.Web.Protocols.Saml.SamlProtocolHandler.BuildSignInResponseCoreWithSerializedToken(HttpSamlRequestMessage httpSamlRequest, WrappedHttpListenerContext context, String relyingPartyIdentifier, SecurityTokenElement signOnTokenElement, Boolean isKmsiRequested, Boolean isApplicationProxyTokenRequired)
at Microsoft.IdentityServer.Web.Protocols.Saml.SamlProtocolHandler.BuildSignInResponseCoreWithSecurityToken(SamlSignInContext context, SecurityToken securityToken, SecurityToken deviceSecurityToken)
at Microsoft.IdentityServer.Web.Protocols.Saml.SamlProtocolHandler.Process(ProtocolContext context)
at Microsoft.IdentityServer.Web.PassiveProtocolListener.ProcessProtocolRequest(ProtocolContext protocolContext, PassiveProtocolHandler protocolHandler)
at Microsoft.IdentityServer.Web.PassiveProtocolListener.OnGetContext(WrappedHttpListenerContext context)
Follow these procedures to integrate your Azure AD IdP with Webex WFO Identity and Access Management (IAM) Service Provider (SP).
Set up Azure AD IDP
- Sign into your Azure portal.
- On the left navigation panel, click on Azure Active Directory.
- In the Azure Active Directory pane, click on Enterprise applications.
- In the Enterprise applications pane, click on New application.
- Click Non-gallery application.
- Enter a name for the Webex WFO application and click Add. The name you enter for Webex WFO is referred to as Webex WFO <Application Name> in these procedures.
- After the application is saved and loaded, click Single sign-on in the left-hand menu and then click SAML.
- In the setup screen, click the pencil icon in the Basic SAML Configuration box.
-
Enter the following values into the fields.
- Identifier (Entity ID) - listed as a prerequisite.
- Reply URL (Assertion Consumer Service URL) - listed as a prerequisite.
Do not enter any data into any other fields.
-
If the Sign on URL is marked as a required field, instead of an optional field, then copy and paste the Service Provider initiated Sign-on URL that was listed as a prerequisite.
-
The Azure AD Identifier for the Webex WFO application in Azure AD is in the Set up <Calabrio ONE Application Name> box in the setup screen. You can use a URL encoder to decode it.
EXAMPLE In this example for United States IAM,
https://www.example.com/123is the Azure AD Identifier that becomeshttps%3A%2F%2Fwww.example.com%2F123when the URL is encoded.NOTE For IdP-Initiated SAML, the Sign on URL field in the app in Azure AD must be empty.
-
- Click Save.
- Navigate to the setup screen.
- Click the pencil icon in the User Attributes & Claims box.
- Click ... the (ellipsis symbol) to edit the claim for http://schemas.xmlsoap.org/ws/2005/05/identity/claims/emailaddress under Additional claims.
- Enter mail in the Name field.
- Delete the pre-populated text in the Namespace field.
- Ensure the Attribute button is selected as the Source (default).
- Ensure user.mail is selected from the Source attribute drop-down list (default).
- Click Save.
- In the left-hand menu click Users and groups.
- Click Add user.
- In the Add Assignment pane, click Users and groups.
- Select the user or group you want to assign to the application for access to Webex WFO. Click Select.
- Click Assign to assign the user or group.
- In the setup screen, click the pencil icon in the SAML Signing Certificate box.
- Enter a notification email in Notification Email field for the certificate expiry reminders.
- Click Save.
- Click Download for Federation Metadata XML.
- Save the metadata file. Then follow the procedure detailed in Set up IAM authentication to connect your IdP to Webex WFO.
Troubleshoot single sign-on
After Webex WFO IAM has been configured to use the application for Webex WFO in Azure AD, you can test the settings to see if single sign-on works for your account. This can be done using the Webex WFO URL provided by Cisco Professional Services Account Representative.
You can test single sign-on from Azure AD.
- Sign into your Azure portal.
- In the left navigation panel, click Azure Active Directory.
- In the Azure Active Directory pane, click Enterprise applications.
- In the Enterprise applications pane, click on the Webex WFO application.
- Click Single sign-on in the left-hand menu.
- Click the Test button in the Test Single Sign-on with <Webex WFO Application Name> box to check if single sign-on is working. You can test using the user who is currently signed in or another user.
Troubleshoot error messages
If an error message appears follow the steps below.
- Copy and paste the specifics from the error message into the What does the error look like? box.
- Click Get resolution guidance.
- Read the guidance to fix the issue.
Related Content
For more information on Microsoft Azure AD see the reference material linked below.
After SAML authentication is configured for your IdP, the metadata needs to be downloaded and exported. Then follow the procedure detailed in Set up IAM authentication to connect your IdP to Webex WFO.
Download Okta SAML Metadata
- Navigate to Applications > Sign On tab.
- Click Identity Provider metadata to start the metadata download.
Download SAML Metadata for other IdPs
Most identity providers allow users to download metadata. To do so, follow the steps detailed below.
- Navigate to your identity provider’s page.
-
Find the button that allows you to download your IdP’s metadata.
NOTE The name of the IdP metadata download button may vary depending on your IdP.
- Save the metadata file then follow the procedure detailed in Set up IAM authentication to connect your IdP to Webex WFO.
Not all IdPs or IdP configurations require service provider certificates.
| IdP | Certificate Required |
|---|---|
|
ADFS |
Yes |
|
Okta |
No |
|
Other IdPs |
Varies by configuration. |
|
Azure AD |
No |
If your IdP or IdP configuration requires a service provider certificate to integrate with Webex WFO, use the signing certificate listed in the prerequisite.
Related topics
- Set up IAM authentication — Follow this procedure to connect your IdP to Webex WFO.
- Log in to Webex WFO (legacy)
- Troubleshoot legacy login issues