Embed Webex WFO in Webex Contact Center Desktop
Webex WFO can be embedded as an application in Webex Contact Center Desktop. This means users can stay in Webex Contact Center Desktop without switching between screens and applications. The embedded solution supports single sign-on (SSO) integrations with Okta and OneLogin. Follow the detailed procedures below to learn how to embed Webex WFO in Webex Contact Center Desktop.
Prerequisites
-
The users you assign in your Okta app or OneLogin app must also exist in Webex WFO.
-
The supported browsers and operating systems are the same as those supported for the Webex Contact Center desktop as specified in System requirements for Webex Contact Center Desktop.
Supported platforms
- Okta
- OneLogin
NOTE This feature has been validated with Okta single sign-on and OneLogin single sign-on.
You can configure multiple single sign-on (SSO) providers. See SSO with multiple IdPs in Webex for more information.
Limitations
-
Not compatible with dark mode, responsiveness, localization, UI and UX, and accessibility available in Webex Contact Center Desktop.
-
Signing out of Webex WFO embedded does not sign you out from Webex Contact Center Desktop.
-
Signing into Webex WFO displays details based on Webex WFO access controls provided by the administrator.
-
Embedding is not currently supported for the standalone QM Basic offering. Embedding is supported for all other offerings of Webex WFO.
IMPORTANT This feature is compatible with the third-party platforms Okta and OneLogin. Their interfaces and functionality may change without notice, which could affect the step-by-step procedures detailed in this article.
Procedures
| Platform | Okta | OneLogin |
|---|---|---|
| Custom Procedures | ||
| 1. | Configure Okta SSO with Webex WFO | Configure OneLogin SSO with Webex WFO |
|
2. |
||
|
3. |
Okta - Get the URLs for your embed links and enable iFraming |
OneLogin - Get the URLs for your embed links and enable iFraming |
|
General Procedures |
||
|
|
||
Okta Procedures
- Sign in to Okta.
NOTE You must be a Super Administrator in Okta to create and configure an app.
- Navigate to Applications > Applications.
- Click Create App Integration.
-
In the Create a new app integration dialog box, configure the field as follows.
Field Configuration Sign-in method
Select SAML 2.0.
-
Click Next.
-
On the Create SAML Integration page General Settings tab, configure the fields as follows.
Field Configuration App name
Enter a unique name.
App logo
(Optional) Upload an image to identify the app in Okta.
App visibility
(Optional) Limit who can see the image in Okta.
- Click Next.
-
On the Configure SAML tab, configure the fields as follows.
Field Configuration General
Single sign-on URL
Refer to the IAM Domain Names table below. Enter your IAM domain.
Leave the Use this for Recipient URL and Destination URL check box selected (default).
IAM Domain Names Australia
https://id-aus.calabriocloud.com/am/Consumer/metaAlias/bravo/calabriospCanada
https://id-ca.calabriocloud.com/am/Consumer/metaAlias/bravo/calabriospEuropean Union
https://id-eu.calabriocloud.com/am/Consumer/metaAlias/bravo/calabriospUnited Kingdom
https://id-uk.calabriocloud.com/am/Consumer/metaAlias/bravo/calabriospUnited States https://id.calabriocloud.com/am/Consumer/metaAlias/bravo/calabriospSingapore
https://id-sgp.calabriocloud.com/am/Consumer/metaAlias/bravo/calabriospAudience URI (SP Entity ID)
Enter calabriosp.
Default Relay State
Leave blank.
Name ID format
Select EmailAddress from the drop-down list.
Application username
Select Email from the drop-down list.
Update application username on
Do not change. This field is set to Create and update by default.
NOTE If Advanced Settings is hidden, click Show Advanced Settings.
Response
Select Signed from the drop-down list.
Assertion Signature
Select Signed from the drop-down list.
Signature Algorithm
Select either RSA-SHA1 or RSA-SHA256.
Digest Algorithm
Select either SHA1 or SHA256.
Assertion Encryption
Select Unencrypted.
Signature Certificate
Leave blank.
Enable Single Logout
Grayed out by default. Leave the Allow application to initiate Single Logout check box cleared (default).
Signed Requests
Grayed out by default. Leave the Validate SAML requests with signature certificates check box cleared (default).
Other Requestable SSO URLs
Leave blank.
Assertion Inline Hook
Do not change. This field is set to None (disabled) by default.
Authentication context class
Select PasswordProtectedTransport.
Honor Force Authentication
Select Yes.
SAML Issuer ID
Leave blank.
Maximum app session lifetime
Leave blank.
Attribute Statements (optional)
Name
Enter mail.
IMPORTANT Do not enter email.
NOTE This setting allows a user’s email address to be properly mapped for SAML assertion. If you do not do this attribute mapping for your external IdP, then a Cisco representative must map the attribute to the user’s email address on your behalf. Contact Cisco Professional Services for assistance.
Name format
Select Unspecified from the drop-down list.
Value
Select user.email.
NOTE You do not need to configure any attributes in the Group Attribute Statements (optional) section.
- Click Next.
-
In the Feedback tab, select the feedback option that is appropriate to your company’s use of Okta.
NOTE Your choice does not affect the ability of Webex WFO to use Okta as an IdP.
- Click Finish. You have successfully created the first of two apps in Okta for Webex WFO.
Download Okta SAML Metadata
After you configure SAML authentication, you need to download your metadata.
- Navigate to Applications > Sign On tab.
-
Copy the metadata URL, then open the URL in a new window.
-
The XML file contains your entityID, X.509Certificate, NameIDFormat, and SingleSignOnService. Save this information in an easy-to-access location. You will use these values during the Enable IAM authentication for your Okta app procedure in Webex WFO later.
-
entityID is Entity ID on the IAM Authentication page in Webex WFO.
X.509Certificate is IDP X.509 Certificate on the IAM Authentication page in Webex WFO.
NameIDFormat is Name ID Format on the IAM Authentication page in Webex WFO.
SingleSignOnService is Single Sign-On Service Endpoint (HTTP-POST/HTTP-Redirect) on the IAM Authentication page in Webex WFO.
-
Enable IAM authentication for your Okta app
-
You need the Administer Tenant permission to access this page. See Manage roles and permissions for QM, Analytics, Insights, and Performance Management for more information.
For more information about the IAM Authentication page, see Set up IAM authentication.
-
Navigate to Webex WFO > Application Management > Administration > IAM Authentication.
- Under Enable Authentication, select the Enable IAM External Authentication Entity (Company Login) check box to allow authentication using an external identity provider.
- Enter the required information in the fields detailed below.
-
Field Description Enable Authentication
Enable IAM External Authentication Entity (Company Login) — Enables authentication using an external IdP.
IAM External Authentication Settings
Entity ID Locate your entity ID in your XML metadata file from Okta.
IDP X.509 Certificate Import, your XML metadata file from Okta. Acceptable file formats are CER, CRT, and CERT.
IMPORTANT The certificate must be Base64 encoded.
Authorization Requests Signed -
Require signed SAML request
Select check box. Name ID Format Enter the following format.
urn:oasis:names:tc:SAML:1.1:nameid-format:emailAddress
Single Sign-On Service Endpoint (HTTP-POST/HTTP-Redirect) Locate your Single Sign-On Service Endpoint in your XML metadata file from Okta.
EXAMPLE
https://dev-111111.oktapreview.com/app/dev-111111_exampletest20220608_1/mpkznqqbkzvTHE3Nc0h7/sso/samlRequire SAML Binding to be HTTP-POST Select check box.
- Click Save.
Assign users to the Okta app
-
Open Okta and navigate to Applications > Applications.
-
Select the Okta app you created during the Create an app in Okta procedure.
-
Under the Assignments tab, click Assign > Assign to People or Assign to Groups.
-
Search for the people or groups you want, then click Assign.
-
Click Done.
Test your connection
Ensure that users assigned to the Okta app are able to login.
NOTE The users you assign in your Okta app must also exist in Webex WFO.
-
Open an incognito window.
-
Navigate to https://login.calabriocloud.com/.
-
Enter the email address of a user assigned to the Okta app.
-
Click Company Login.
-
You are routed to Okta. Enter your Okta credentials and login.
This is the second application you need to create in Okta.
Turn on SSO in Webex Control Hub and download metadata
-
Sign in to Webex Control Hub.
-
Navigate to Security > Authentication.
-
Select your IdP.
-
Select Self-signed by Cisco or Signed by a public certificate authority.
BEST PRACTICE Cisco recommends selecting Self-signed by Cisco.
-
Download the metadata file. The default Webex Control Hub metadata filename is
idb-meta-<org-ID>-SP.xml.
NOTE For more information see the Download the Webex metadata to your local system chapter in the Configure single sign-on in Control Hub with Okta help article.
Configure Okta for Webex services
-
Open Okta and navigate to Applications > Applications.
-
Click Browse App Catalog.
-
Search for and select Cisco Webex (SCIM, SAML, SWA).
-
Click Add Integration.
-
On the Add Cisco Webex page General Settings tab, configure the fields as follows.
Field Configuration Application label
Enter a unique name.
BEST PRACTICE Enter your organization's name in Webex WFO.
Application Visibility
(Optional)
Browser plugin auto-submit
Select Automatically log in when user lands on login page.
-
Click Next.
-
In the General Settings tab, click SAML 2.0.
-
Go to the Credentials Details section, towards the end of the page.
-
Select Email from the Application username format drop-down list.
-
In your browser, open the metadata file that you downloaded from Webex Control Hub.
-
Navigate back to the General Settings tab > SAML 2.0.
-
In the Advanced Sign-on Settings section, enter the Entity ID and Assertion Consumer Service location that you copied from the metadata file you downloaded.
-
In the Credentials Details section, select Email from the Application username format drop-down list.
-
Select Create and update from the Update application username on drop-down list.
-
Click Done.
NOTE For more information see the Configure Okta for Webex services chapter in the Configure single sign-on in Control Hub with Okta help article.
Import the IdP metadata and enable SSO
-
Sign in to Webex Control Hub.
- Navigate to Applications > Sign On tab.
-
Copy the metadata URL, then open the URL in a new window.
-
In Webex Control Hub, navigate to Management > Security > Authentication > Identity provider tab.
-
Click Activate SSO.
-
Select SAML on the Step 1: Select an identity provider page. Click Next and proceed through the remaining steps.
-
On Step 3: Configure IdP metadata, upload your IdP's metadata file.
-
Then select Less secure: Not signed, self-signed or private CA signed IdP metadata file. Selecting this option means your certificate only needs to be renewed once every five years.
-
Click Next until you complete all the steps.
-
Select Test SSO setup, and when a new browser tab opens, authenticate with the IdP by signing in.
-
Return to the Webex Control Hub browser tab.
-
If the test was successful, select Successful test. Turn on SSO and click Next.
-
If the test was unsuccessful, select Unsuccessful test. Turn on SSO and click Next.
-
NOTE For more information see the Import the IdP metadata and enable single sign-on after a test chapter in the Configure single sign-on in Control Hub with Okta help article.
Assign users to the Webex app
IMPORTANT The users you assign in your Okta app must also exist in Webex WFO. Ensure that the email addresses entered here are tied to user accounts in Webex WFO.
-
Open Okta and navigate to Applications > Applications.
-
Select the Okta app you created during the Create an app in Okta procedure.
-
Under the Assignments tab, click Assign > Assign to People or Assign to Groups.
-
Search for the people or groups you want, then click Assign.
-
Click Done.
Test your connection
Ensure that users assigned to the Okta app are able to login.
-
Open an incognito window.
-
Navigate to https://admin.webex.com/.
-
Enter the login credentials of a user assigned to the Okta app.
-
You are then routed to Okta. Enter your Okta credentials and sign in.
In this procedure you will enable iFrame embedding, copy Okta's embedded link, and copy the MyTime embed link (MyTime is also referred to as MySchedule).
-
Open Okta and within the Admin Console navigate to Customizations > Other. Go to the iFrame Embedding section.
-
Select the Allow iFrame embedding check box.
-
Click Save.
-
Navigate to Applications > Applications > select your WFO application from the list > General tab.
-
Copy the Embed Link in the App Embed Link section of the General tab.
-
To get the MyTime embed link, navigate to Webex WFO > WFM > MyTime. MyTime opens in a new browser window or tab.
-
Copy the MyTime URL from the address bar.
EXAMPLE https://mtdemousce01.teleopticloud.com/web/MyTime#Schedule
Next, complete the Paste app embed links in custom layouts procedures.
OneLogin Procedures
Add Calabrio ONE app in OneLogin
-
Sign in to OneLogin.
-
Navigate to Applications > Applications.
-
Click Add App.
-
Search for Calabrio.
-
Select the Calabrio ONE (OneLogin) app.
IMPORTANT Ensure that you select the Calabrio ONE (OneLogin) app depicted in the image above. Do not select Calabrio (OneLogin, Inc.).
-
Click Save to add the Calabrio ONE (OneLogin) app. No custom configuration is required for the Calabrio ONE (OneLogin) app.
Download SAML Metadata in OneLogin
After you add the Calabrio ONE app, you need to download your metadata.
- Navigate to Applications > Applications.
- Click Download JSON and save the file.
-
The XML file contains your entityID, X.509Certificate, NameIDFormat, and SingleSignOnService. Save this information in an easy-to-access location. You will use these values during a later procedure.
-
entityID is Entity ID on the IAM Authentication page in Webex WFO.
X.509Certificate is IDP X.509 Certificate on the IAM Authentication page in Webex WFO.
NameIDFormat is Name ID Format on the IAM Authentication page in Webex WFO.
SingleSignOnService is Single Sign-On Service Endpoint (HTTP-POST/HTTP-Redirect) on the IAM Authentication page in Webex WFO.
-
Enable IAM authentication for your OneLogin app
You need the Administer Tenant permission to access this page. See Manage roles and permissions for QM, Analytics, Insights, and Performance Management for more information. For more information about the IAM Authentication page, see Set up IAM authentication.
-
Navigate to Webex WFO > Application Management > Administration > IAM Authentication.
- Under Enable Authentication, select the Enable IAM External Authentication Entity (Company Login) check box to allow authentication using an external identity provider.
-
Enter the required information in the fields detailed below.
Field Description Enable Authentication
Enable IAM External Authentication Entity (Company Login) — This enables authentication using an external IdP.
IAM External Authentication Settings
Entity ID Locate your entity ID in your XML metadata file from OneLogin.
IDP X.509 Certificate Import, your metadata file from OneLogin. Acceptable file formats are CER, CRT, and CERT.
IMPORTANT The certificate must be Base64 encoded.
Authorization Requests Signed -
Require signed SAML request
Select check box. Name ID Format Enter the following format.
urn:oasis:names:tc:SAML:1.1:nameid-format:emailAddress
Single Sign-On Service Endpoint (HTTP-POST/HTTP-Redirect) Locate your Single Sign-On Service Endpoint in your metadata file from OneLogin.
EXAMPLE
https://wxcc2.onelogin.com/trust/saml2/http-post/sso/11111111-bbbb-3333-cccc-555555555555Require SAML Binding to be HTTP-POST Select check box.
- Click Save.
Add your OneLogin app to Webex Control Hub (Part One)
-
Open Webex Control Hub.
-
Navigate to Security > Authentication.
-
Click Add an IdP.
-
Click SAML and then click Next on the Step 1: Select an identity provider page.
-
Select Self-signed by Cisco or Signed by a public certificate authority on the Step 2: Select and export a certificate page.
BEST PRACTICE Cisco recommends selecting Self-signed by Cisco.
-
Download the metadata file. The default Webex metadata filename is
idb-meta-<unique identifier>-SP.xml. This file will be used for a later procedure.
Create a second OneLogin app
-
Open OneLogin.
-
Navigate to Applications > Applications.
-
Click Add App.
-
Search SAML Custom Connector and select SAML Custom Connector (Advanced) from the list.
IMPORTANT Ensure that you select the SAML Custom Connector (Advanced) application depicted in the image above.
-
Open the Configuration page from the left navigation bar.
-
Open the Webex metadata file from the previous procedure (Add your OneLogin app to Webex Control Hub (Part One)). Enter the information from the metadata file to the following fields.
-
Enter the EntityID from the file in the Audience (EntityID) field.
-
Enter the AssertionconsumerService Location from the file in the Recipient field.
-
Enter the AssertionconsumerService Location from the file in the ACS (Consumer) URL Validator field.
-
Enter the AssertionconsumerService Location from the file the ACS (Consumer) URL field.
-
-
Click Save to add the SAML Custom Connector (Advanced) app.
-
Click More Actions > SAML Metadata and save the file. You will use this file in the next procedure.
Add your OneLogin app to Webex Control Hub (Part Two)
-
Go back to Webex Control Hub.
-
On Step 3: Configure IdP metadata, upload your IdP's metadata file.
-
Then you must select Less secure: Not signed, self-signed or private CA signed IdP metadata file.
-
Click Next until you arrive at the Step 5: Test your SSO setup page.
-
Select Test SSO setup, and when a new browser tab opens, authenticate with the IdP by signing in.
-
Return to the Control Hub browser tab.
-
If the test was successful, select Successful test. Turn on SSO and click Next.
-
If the test was unsuccessful, select Unsuccessful test. Turn on SSO and click Next.
-
NOTE For more information see the Download the Webex metadata to your local system chapter and the Import the IdP metadata and enable single sign-on after a test chapter in the Configure single sign-on in Control Hub with Okta help article.
Add users in OneLogin
IMPORTANT The users you create in OneLogin must also exist in Webex WFO. Ensure that the email addresses entered here are tied to user accounts in Webex WFO.
-
Open OneLogin.
-
Navigate to Users > Users.
-
Click New User.
-
On the New User configuration page, enter all required information.
-
Click Save User. The user's configuration page opens.
-
Click Applications.
-
Click the Applications + icon. The Assign new login to [user's name] dialog box opens.
-
Select SAML Custom connector (Advanced) from the Select application drop-down list.
-
Click Save User. The Edit SAML Custom connector for [user's name] dialog box opens.
-
Ensure that the Allow the user to sign in check box is selected.
-
Click Save.
Test your connection
Ensure that users assigned to the OneLogin application are able to login.
-
Open the Step 5: Test your SSO setup page in Webex Control Hub
-
Click Copy URL to clipboard.
-
Open an incognito window.
-
Paste the URL you just copied in the incognito window.
-
Enter your login credentials.
In this procedure you will locate and copy your subdomain and your app ID.
-
Navigate to Applications > Applications.
-
Open your Calabrio ONE (OneLogin) app.
-
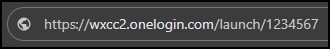
Copy the subdomain and app ID directly from your browser's address bar.
EXAMPLE The subdomain is the text that appears before the domain. In this example the subdomain is wxcc2.
The app ID is the string of numbers that appear after/apps/. In this example it is 40----7. -
Create your custom embed URL link using this format. This is your Workforce Optimization embed URL link. You will use this embed link URL in a later procedure.
https://[subdomain].onelogin.com/launch/[appID]
-
In OneLogin, navigate to Settings > Account Settings > Basic.
-
In the Framing Protection section, select the Allow framing from the following origins.
-
In a separate window, open Webex Contact Center Desktop, and then copy the URL.
-
Go back to your OneLogin window Basic page.
-
In the Content Security Policy - Origin URLs text box, paste your Webex Contact Center Desktop URL.
-
Select the Fall back to allowing ALL framing in those browsers (less secure) check box.
-
Click Save.
-
To get the MySchedule (also known as MyTime) embed link navigate to Webex WFO > WFM > MyTime. MyTime opens in a new browser window or tab.
-
Copy the MyTime URL from the address bar.
EXAMPLE https://mtdemousce01.teleopticloud.com/web/MyTime#Schedule
General Procedures
Create custom layouts
In this procedure you will create the following four custom layouts.
- Workforce Optimization (WFO) layout for the agent persona
- MySchedule layout for the agent persona
- Workforce Optimization layout for the Supervisor persona and the Supervisor and Agent persona
- MySchedule layout for the Supervisor persona and the Supervisor and Agent persona
JSON-formatted code snippets are provided to you below.
NOTE See Create custom desktop layout for more information.
Create the Workforce Optimization layout for the Agent persona
{
"nav": {
"label": "WorkForce Optimization",
"icon": "primary-participant-bold",
"iconActive": "primary-participant-filled",
"iconType": "momentumdesign",
"navigateTo": "WFO-Profile",
"align": "top",
"isDefaultLandingPage": true
},
"page": {
"id": "iframe",
"widgets": {
"left": {
"comp": "agentx-wc-iframe",
"attributes": {
"src": "https://integrator-4748321.okta.com/home/integrator-4748321_webexwfo_1/0oat7pzdl9YJapVGe697/alnt7qhm618dFX46u697"
}
}
},
"layout": {
"areas": [
[
"left"
]
],
"size": {
"cols": [
1
],
"rows": [
1
]
}
}
}
},- Copy the code snippet above.
- Replace the
"src":url in line 17 with your Workforce Optimization (Webex WFO) embed URL link. - Save the file.
Create the MySchedule layout for the Agent persona
{
"nav": {
"label": "My Schedule",
"icon": "webex-meetings-bold",
"iconActive": "webex-meetings-filled",
"iconType": "momentumdesign",
"navigateTo": "WFO-Schedule",
"align": "top"
},
"page": {
"id": "iframe",
"widgets": {
"left": {
"comp": "agentx-wc-iframe",
"attributes": {
"src": "https://mtdemousce01.teleopticloud.com/web/mytime#Schedule"
}
}
},
"layout": {
"areas": [
[
"left"
]
],
"size": {
"cols": [
1
],
"rows": [
1
]
}
}
}
},- Copy the code snippet above.
- Replace the
"src":url in line 16 with your MySchedule embed URL link. - Save the file.
Create the Workforce Optimization layout for the Supervisor persona and the Supervisor and Agent persona
{
"nav": {
"label": "WorkForce Optimization",
"icon": "webex-teams-bold",
"iconType": "momentumdesign",
"iconActive": "webex-teams-filled",
"navigateTo": "WFO",
"align": "top",
"isDefaultLandingPage": true
},
"page": {
"id": "iframe",
"widgets": {
"left": {
"comp": "agentx-wc-iframe",
"attributes": {
"src": "https://integrator-4748321.okta.com/home/integrator-4748321_webexwfo_1/0oat7pzdl9YJapVGe697/alnt7qhm618dFX46u697"
}
}
},
"layout": {
"areas": [
[
"left"
]
],
"size": {
"cols": [
1
],
"rows": [
1
]
}
}
}
},- Copy the code snippet above.
- Replace the
"src":url in line 17 with your Workforce Optimization embed URL link. - Save the file.
Create the MySchedule layout for the Supervisor persona and the Supervisor and Agent persona
{
"nav": {
"label": "Schedule",
"icon": "webex-meetings-bold",
"iconActive": "webex-meetings-filled",
"iconType": "momentumdesign",
"navigateTo": "WFO-Schedule",
"align": "top"
},
"page": {
"id": "iframe",
"widgets": {
"left": {
"comp": "agentx-wc-iframe",
"attributes": {
"src": "https://mtdemousce01.teleopticloud.com/web/mytime#Schedule"
}
}
},
"layout": {
"areas": [
[
"left"
]
],
"size": {
"cols": [
1
],
"rows": [
1
]
}
}
}
}- Copy the code snippet above.
- Replace the
"src":url in line 16 with your MySchedule embed URL link. - Save the file.

The following image is an example code snippet for the MySchedule custom layout.

Administer the layout
Administer the layouts for Agent, Supervisor, and Supervisor and Agent personas in Webex Control Hub - https://admin.webex.com/wxcc/desktop-experience/desktop-profiles.
-
Open Webex Contact Center Control Hub.
-
Navigate to Contact Center > Desktop Layouts.
-
Click Create Desktop Layout.
-
Upload one of the custom desktop layouts files from the previous procedure.
-
Enable the Active toggle in the top-right corner of the page.
-
Navigate to Teams.
-
Select a team from the list.
-
In the Team settings section, select your custom desktop layout from the Desktop layout drop-down list.
-
Repeat for all custom layout files.
Test layout
-
Sign in as all the personas. Always keep the left navigation pane collapsed.
-
Select the Webex WFO icon from the left-navigation pane. Confirm you see the Webex WFO icon.
-
Select the MySchedule icon from the left-navigation pane. confirm you see the MySchedule icon.
BEST PRACTICE Speed up the embed page by changing the Webex WFO landing page. Follow the Assign landing pages to users procedure.
NOTE This setting can be applied as a browser policy by the IT organization, meaning agents and supervisors do not need to apply it individually.
-
Navigate to Settings > Privacy & Security > Cookies and Site Data > Manage Exceptions.
-
Add the following URLS.
-
https://login.calabriocloud.com
-
Your Okta Embed link: (example) https://integrator-4748321.okta.com
-
Your OneLogin Embed link: (example) https://wxcc.onelogin.com/launch/3980125
-
http://mtdemousce01.teleopticloud.com
-
https://id.calabriocloud.com
-
-
Click Save.